Introduction
In today’s rapidly evolving digital landscape, maintaining a robust security posture is more critical than ever. One of the most fundamental yet often overlooked aspects of cybersecurity is the timely patching of third-party software. As organizations increasingly rely on a diverse array of applications to drive their operations, the need to automate 3rd party patching has become paramount. This comprehensive guide will delve into the intricacies of automating third-party patching, exploring its importance, challenges, and the transformative impact it can have on your organization’s security infrastructure.
Third-party applications, while essential for productivity and innovation, often introduce vulnerabilities that can be exploited by malicious actors. The sheer volume and frequency of patches released for these applications make manual patching processes not only time-consuming but also prone to human error. By implementing automated 3rd party patching solutions, organizations can significantly enhance their security posture, reduce operational overhead, and ensure compliance with industry regulations.
Throughout this article, we’ll explore the various facets of automating third-party patching, from understanding its fundamental concepts to implementing best practices and leveraging cutting-edge tools. Whether you’re an IT professional looking to optimize your patching processes or a business leader seeking to bolster your organization’s cybersecurity defenses, this guide will provide you with the knowledge and insights needed to navigate the complex world of automated 3rd party patching.
Understanding 3rd Party Patching
What is 3rd Party Software?
Before diving into the intricacies of automated 3rd party patching, it’s crucial to understand what exactly constitutes third-party software. In essence, third-party software refers to any application or program that is not developed by the operating system vendor or the organization using it. These applications are created by external vendors to provide specific functionalities or services that enhance the capabilities of your systems.
Common examples of third-party software include:
- Productivity suites (e.g., Microsoft Office, Google Workspace)
- Web browsers (e.g., Chrome, Firefox, Safari)
- PDF readers (e.g., Adobe Acrobat)
- Media players (e.g., VLC, QuickTime)
- Collaboration tools (e.g., Slack, Zoom)
- Design software (e.g., Adobe Creative Suite)
While these applications greatly enhance productivity and functionality, they also introduce potential security vulnerabilities that need to be addressed through regular patching.
Why is 3rd Party Patching Crucial?
The importance of 3rd party patching cannot be overstated in today’s cybersecurity landscape. Here are several key reasons why organizations must prioritize this critical aspect of their security strategy:
- Vulnerability Mitigation: Third-party applications often contain security flaws that can be exploited by cybercriminals. Timely patching addresses these vulnerabilities, reducing the attack surface of your systems.
- Compliance Requirements: Many industry regulations and standards (e.g., HIPAA, PCI DSS) mandate regular patching of all software, including third-party applications. Failing to do so can result in non-compliance and potential penalties.
- Performance Improvements: Patches often include not only security fixes but also performance enhancements and bug fixes, ensuring that your applications run smoothly and efficiently.
- Data Protection: Unpatched vulnerabilities can lead to data breaches, potentially exposing sensitive information. Regular patching helps safeguard your organization’s and customers’ data.
- Reputation Management: Security incidents resulting from unpatched vulnerabilities can severely damage an organization’s reputation. Proactive patching demonstrates a commitment to security and helps maintain stakeholder trust.
Common Vulnerabilities in 3rd Party Applications
Third-party applications are often targeted by cybercriminals due to their widespread use and the potential for exploiting known vulnerabilities. Some of the most common types of vulnerabilities found in these applications include:
- Buffer Overflows: These occur when a program writes more data to a buffer than it can hold, potentially allowing attackers to execute arbitrary code.
- SQL Injection: This vulnerability allows attackers to manipulate database queries, potentially gaining unauthorized access to sensitive data.
- Cross-Site Scripting (XSS): XSS vulnerabilities enable attackers to inject malicious scripts into web applications, compromising user interactions.
- Remote Code Execution: These vulnerabilities allow attackers to execute arbitrary code on a target system, often leading to full system compromise.
- Privilege Escalation: These flaws enable attackers to gain higher-level permissions than they should have, potentially leading to unauthorized access to critical systems.
By implementing an automated 3rd party patching solution, organizations can rapidly address these vulnerabilities as patches become available, significantly reducing the window of opportunity for potential attackers.
| Vulnerability Type | Potential Impact | Mitigation through Patching |
|---|---|---|
| Buffer Overflow | Code execution, system crash | High |
| SQL Injection | Data theft, data manipulation | Very High |
| Cross-Site Scripting | Session hijacking, phishing | High |
| Remote Code Execution | Full system compromise | Critical |
| Privilege Escalation | Unauthorized access, data breach | High |
As we delve deeper into the concept of automating 3rd party patching, it becomes clear that this approach is not just a convenience but a necessity in today’s complex IT environments. The next section will explore the specific need for automation in the patching process and how it addresses the challenges faced by organizations in maintaining a secure and compliant software ecosystem.
The Need for Automation in 3rd Party Patching
As organizations grow and their IT infrastructures become more complex, the need to automate 3rd party patching becomes increasingly apparent. Manual patching processes, while once sufficient for smaller environments, are no longer viable for modern, dynamic IT landscapes. Let’s explore the limitations of manual patching and how automation addresses these challenges.
Limitations of Manual Patching Processes
Manual patching processes suffer from several significant drawbacks:
- Time-consuming: Manually identifying, downloading, testing, and deploying patches for numerous third-party applications across multiple systems is an enormously time-intensive task.
- Error-prone: Human error in manual patching can lead to missed vulnerabilities or improperly applied patches, potentially causing system instability or leaving security gaps.
- Inconsistent: Manual processes often lead to inconsistent patching across the organization, with some systems receiving updates while others are overlooked.
- Lack of scalability: As the number of systems and applications grows, manual patching becomes increasingly unfeasible and resource-intensive.
- Poor visibility: Manual processes often lack comprehensive reporting and visibility into the overall patch status across the organization.
Risks Associated with Delayed Patching
The consequences of delayed patching can be severe and far-reaching. Some of the key risks include:
- Extended vulnerability windows: The longer a system remains unpatched, the more time attackers have to exploit known vulnerabilities.
- Increased attack surface: Unpatched systems provide more entry points for potential attackers, expanding the overall attack surface of the organization.
- Compliance violations: Failure to patch systems in a timely manner can result in non-compliance with industry regulations and standards.
- Data breaches: Exploited vulnerabilities can lead to unauthorized access and potential theft of sensitive data.
- Reputational damage: Security incidents resulting from unpatched vulnerabilities can severely impact an organization’s reputation and customer trust.
How Automation Addresses These Challenges
Implementing automated 3rd party patching solutions offers numerous benefits that directly address the limitations of manual processes:
- Efficiency: Automation dramatically reduces the time and effort required to manage the patching process, allowing IT teams to focus on more strategic initiatives.
- Consistency: Automated solutions ensure that patches are applied consistently across all systems, reducing the risk of overlooked or improperly patched applications.
- Scalability: As organizations grow, automated patching solutions can easily scale to accommodate increasing numbers of systems and applications.
- Improved visibility: Automated tools provide comprehensive reporting and real-time visibility into the patch status of all systems, enabling better decision-making and risk management.
- Reduced human error: By minimizing manual intervention, automation reduces the likelihood of errors in the patching process.
- Faster response times: Automated systems can quickly identify and deploy critical patches, significantly reducing the window of vulnerability.
| Aspect | Manual Patching | Automated Patching |
|---|---|---|
| Time Efficiency | Low | High |
| Consistency | Variable | High |
| Scalability | Poor | Excellent |
| Visibility | Limited | Comprehensive |
| Error Rate | High | Low |
| Response Time | Slow | Fast |
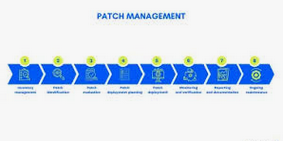
Key Components of Automated 3rd Party Patching
To effectively automate 3rd party patching, organizations need to implement a comprehensive solution that incorporates several key components. These components work together to create a robust, efficient, and secure patching process.
Patch Management Software
At the heart of any automated 3rd party patching solution is the patch management software. This central component orchestrates the entire patching process and typically includes the following features:
- Patch discovery: Automatically identifies available patches for installed third-party applications.
- Patch assessment: Evaluates patches for relevance and potential impact on existing systems.
- Deployment scheduling: Allows for the planning and scheduling of patch deployments to minimize disruption.
- Rollback capabilities: Enables the reversal of patch installations in case of compatibility issues or unforeseen problems.
- Reporting and analytics: Provides detailed insights into patch status, compliance, and overall security posture.
Vulnerability Scanners
Vulnerability scanners play a crucial role in identifying potential security weaknesses in third-party applications. These tools:
- Continuously scan systems for known vulnerabilities
- Compare installed software versions against databases of known vulnerabilities
- Prioritize vulnerabilities based on severity and potential impact
- Integrate with patch management software to streamline the remediation process
Patch Deployment Tools
Efficient patch deployment is essential for successful automation. Patch deployment tools facilitate:
- Remote installation of patches across multiple systems
- Bandwidth-optimized distribution of patch files
- Scheduling of deployments during maintenance windows
- Handling of system reboots when required by patches
Reporting and Analytics
Comprehensive reporting and analytics capabilities are crucial for maintaining visibility and ensuring compliance. Key features include:
- Real-time dashboards showing patch status across the organization
- Detailed reports on patch compliance, success rates, and potential issues
- Historical data for trend analysis and auditing purposes
- Integration with security information and event management (SIEM) systems for broader security insights
By leveraging these key components, organizations can create a robust automated 3rd party patching solution that significantly enhances their security posture while reducing the operational burden on IT teams. In the next section, we’ll explore the steps involved in implementing such a solution.
Steps to Automate 3rd Party Patching
Implementing an automated 3rd party patching solution requires careful planning and execution. By following these steps, organizations can establish a robust and efficient patching process that enhances their overall security posture.
Assessing Your Current Patching Process
Before implementing automation, it’s crucial to evaluate your existing patching procedures:
- Inventory your systems and applications: Create a comprehensive list of all third-party software in use across your organization.
- Identify current patching methods: Document how patches are currently managed, including manual processes and any existing automation.
- Analyze pain points: Determine where your current process falls short, such as delays, inconsistencies, or resource constraints.
- Set goals: Define clear objectives for your automated patching solution, such as reduced patching time or improved compliance rates.
Choosing the Right Automation Tools
Selecting appropriate tools is critical for successful automation of 3rd party patching:
- Research available solutions: Investigate various patch management platforms, considering factors like compatibility, scalability, and ease of use.
- Evaluate features: Look for key capabilities such as automatic patch discovery, testing environments, and robust reporting.
- Consider integration: Ensure the chosen solution can integrate with your existing IT infrastructure and security tools.
- Test before committing: Whenever possible, run a pilot program or proof of concept to verify the tool’s effectiveness in your environment.
Implementing Automated Patch Discovery
Effective patch discovery is the foundation of automated 3rd party patching:
- Configure asset inventory: Ensure your automation tool has a complete and up-to-date inventory of all systems and applications.
- Set up patch sources: Configure the tool to monitor official vendor sites and reputable third-party repositories for new patches.
- Establish scanning schedules: Determine how frequently your systems will be scanned for new patches and vulnerabilities.
- Implement categorization: Set up a system to categorize patches based on criticality and relevance to your environment.
Setting Up Automated Patch Testing
Thorough testing is crucial to prevent patches from causing issues in your production environment:
- Create a test environment: Set up a separate environment that mirrors your production systems for safe patch testing.
- Define testing protocols: Establish clear procedures for testing patches, including compatibility checks and performance evaluations.
- Automate test workflows: Configure your patch management tool to automatically deploy patches to the test environment and run predefined tests.
- Implement approval processes: Set up workflows for reviewing test results and approving patches for production deployment.
Configuring Automated Patch Deployment
Once patches have been tested and approved, automate their deployment to production systems:
- Define deployment policies: Establish rules for when and how patches should be deployed, considering factors like business hours and system criticality.
- Set up deployment groups: Organize systems into logical groups for phased rollouts, reducing the risk of widespread issues.
- Configure bandwidth management: Implement controls to ensure patch deployments don’t overwhelm network resources.
- Establish fallback procedures: Automate rollback processes in case deployed patches cause unexpected issues.
Establishing Automated Reporting and Monitoring
Comprehensive reporting and monitoring are essential for maintaining visibility and ensuring the effectiveness of your automated patching process:
- Set up dashboards: Create customized dashboards that provide at-a-glance views of your patching status and compliance levels.
- Configure alerts: Establish automated notifications for critical events, such as failed patch deployments or newly discovered vulnerabilities.
- Schedule regular reports: Set up automated reports to be generated and distributed to relevant stakeholders on a regular basis.
- Integrate with SIEM: Connect your patch management system with your Security Information and Event Management (SIEM) solution for comprehensive security monitoring.
Best Practices for Automating 3rd Party Patching
To maximize the effectiveness of your automated 3rd party patching solution, consider implementing these best practices:
Prioritizing Critical Patches
Not all patches are created equal. Implement a system to prioritize patches based on:
- Vulnerability severity: Focus on patches that address critical or high-severity vulnerabilities first.
- Exploit availability: Prioritize patches for vulnerabilities with known exploits in the wild.
- Asset importance: Give higher priority to patches for systems that handle sensitive data or are critical to business operations.
Creating a Patch Testing Environment
A robust testing environment is crucial for safe and effective patching:
- Mimic production: Ensure your test environment closely resembles your production systems in terms of configuration and software.
- Use virtualization: Leverage virtualization technologies to create easily replicable test environments.
- Automate testing: Implement automated testing scripts to verify system stability and application functionality post-patching.
- Document thoroughly: Maintain detailed records of all test results for auditing and troubleshooting purposes.
Implementing Rollback Procedures
Despite thorough testing, issues can still arise. Ensure you have robust rollback capabilities:
- Create system snapshots: Take snapshots of systems before applying patches to facilitate easy rollbacks if needed.
- Automate rollback triggers: Set up automated monitoring to detect issues post-patching and initiate rollback procedures if necessary.
- Test rollback processes: Regularly verify that your rollback procedures work as expected.
Maintaining an Up-to-Date Inventory
An accurate and current inventory is fundamental to effective patch management:
- Implement asset discovery: Use automated tools to continuously discover and catalog all devices and software in your environment.
- Track software versions: Maintain detailed records of installed software versions across all systems.
- Monitor for unauthorized software: Set up alerts for the installation of unapproved or potentially vulnerable software.
Regular Auditing and Compliance Checks
Continuous evaluation ensures your patching process remains effective and compliant:
- Conduct regular audits: Perform periodic reviews of your patching process, including success rates and time-to-patch metrics.
- Verify compliance: Regularly check that your patching practices align with relevant industry standards and regulations.
- Review and update policies: Continuously refine your patching policies based on audit results and changing security landscapes.
By following these steps and best practices, organizations can significantly enhance their security posture through effective automation of 3rd party patching. In the next section, we’ll explore some of the challenges that may arise during this process and strategies to overcome them.
Challenges in Automating 3rd Party Patching
While automating 3rd party patching offers numerous benefits, it’s not without its challenges. Being aware of these potential hurdles and having strategies to address them is crucial for successful implementation.
Dealing with Application Compatibility Issues
One of the most common challenges in automating 3rd party patching is ensuring that patches don’t break existing applications or systems. To mitigate this risk:
- Comprehensive testing: Implement rigorous testing procedures in a controlled environment that closely mimics your production setup.
- Phased rollouts: Deploy patches to a small subset of systems first, gradually expanding to the entire infrastructure.
- Application dependency mapping: Maintain a clear understanding of how different applications interact to predict potential compatibility issues.
- Vendor communication: Stay in close contact with software vendors for early warnings about potential compatibility problems.
Managing Patches for Legacy Systems
Legacy systems often pose unique challenges in automated patching processes:
- Limited vendor support: Older systems may no longer receive regular patches from vendors.
- Compatibility concerns: Legacy systems may not be compatible with modern patching tools or newer patch versions.
- Business criticality: Many legacy systems are critical to business operations, making downtime for patching problematic.
To address these challenges:
- Implement compensating controls like network segmentation for systems that can’t be easily patched.
- Consider virtualization or containerization to isolate legacy systems while enabling easier management.
- Develop a long-term strategy for modernizing or replacing legacy systems where possible.
Handling Patches that Require User Interaction
Some patches, particularly for end-user applications, may require user interaction or cause visible changes. To manage this:
- User communication: Develop clear communication channels to inform users about upcoming patches and any required actions.
- Scheduling flexibility: Allow some user control over when patches are applied, within defined compliance windows.
- Remote assistance: Provide remote support options for users who encounter issues during or after patching.
- Automation scripts: Where possible, develop scripts to handle common user interactions automatically.
Balancing Security with Business Continuity
Striking the right balance between timely patching and minimizing business disruption can be challenging. Consider these strategies:
- Risk-based approach: Prioritize patches based on the criticality of the vulnerability and the importance of the affected systems.
- Maintenance windows: Schedule regular maintenance windows for patching, coordinating with business units to minimize impact.
- High-availability configurations: Implement redundant systems where possible to allow for patching without service interruption.
- Patch batching: Group non-critical patches to reduce the frequency of system updates and reboots.
Tools and Solutions for Automated 3rd Party Patching
A variety of tools are available to help organizations automate their 3rd party patching processes. Here’s an overview of some popular solutions and key features to consider:
Overview of Popular Patch Management Tools
| Tool | Key Features | Best Suited For |
|---|---|---|
| Microsoft System Center Configuration Manager (SCCM) | Comprehensive management, integrates with Windows ecosystems | Large enterprises with primarily Windows environments |
| Ivanti Patch for Windows | Extensive third-party application support, customizable policies | Organizations with diverse software portfolios |
| ManageEngine Patch Manager Plus | Cross-platform support, cloud and on-premises options | Small to medium-sized businesses with mixed environments |
| SolarWinds Patch Manager | Integration with broader IT management tools, detailed reporting | Midsize to large organizations using other SolarWinds products |
| Automox | Cloud-native, API-first approach, cross-platform | Organizations looking for a modern, cloud-based solution |
Comparison of Key Features
When evaluating patch management tools for automating 3rd party patching, consider the following key features:
- Patch discovery and assessment: Ability to automatically identify available patches and assess their relevance.
- Multi-platform support: Capability to manage patches across various operating systems and device types.
- Customizable policies: Flexibility to create and enforce patching policies tailored to your organization’s needs.
- Reporting and compliance: Comprehensive reporting features to track patching status and demonstrate compliance.
- Integration capabilities: Ability to integrate with existing security and IT management tools.
- Scalability: Capacity to grow with your organization and handle large numbers of endpoints.
- Deployment options: Availability of on-premises, cloud-based, or hybrid deployment models.
Considerations for Choosing the Right Solution
When selecting a tool to automate 3rd party patching, keep these factors in mind:
- Environment complexity: Consider the diversity of your IT environment, including operating systems and applications in use.
- Scalability needs: Ensure the solution can handle your current infrastructure and accommodate future growth.
- Ease of use: Look for intuitive interfaces and workflows to minimize the learning curve for your IT team.
- Total cost of ownership: Consider not just the initial price, but ongoing costs including training, maintenance, and potential infrastructure changes.
- Vendor support and community: Evaluate the level of support provided by the vendor and the availability of community resources.
- Compliance requirements: Ensure the tool can help meet your specific industry regulations and compliance needs.
By carefully considering these factors and thoroughly evaluating available options, organizations can select the most appropriate tool to automate their 3rd party patching processes effectively. In the next section, we’ll explore how to measure the success of your automated patching implementation.
Measuring the Success of Automated 3rd Party Patching
Implementing an automated 3rd party patching solution is just the beginning. To ensure ongoing effectiveness and justify the investment, it’s crucial to measure and track the success of your patching efforts. Here are key areas to focus on:
Key Performance Indicators (KPIs)
Establish and monitor these KPIs to gauge the effectiveness of your automated 3rd party patching process:
- Patch Coverage Rate: The percentage of systems that have successfully received and installed available patches.
- Mean Time to Patch (MTTP): The average time between a patch release and its successful installation across your environment.
- Patch Failure Rate: The percentage of patch installations that fail or cause issues.
- Vulnerability Exposure Time: The duration between a vulnerability’s public disclosure and its remediation in your environment.
- Patch Compliance Rate: The percentage of systems that meet your defined patching policies and timelines.
Patch Compliance Rates
Maintaining high patch compliance is crucial for a robust security posture. To effectively track and improve compliance:
- Define clear policies: Establish specific timelines for applying patches based on their criticality.
- Regular audits: Conduct frequent checks to ensure systems are adhering to patching policies.
- Automated reporting: Utilize your patch management tool’s reporting features to generate compliance reports automatically.
- Trend analysis: Track compliance rates over time to identify patterns and areas for improvement.
Mean Time to Patch
Reducing the mean time to patch is a critical goal for any automated patching solution. To optimize this metric:
- Streamline approval processes: Implement efficient workflows for patch testing and approval.
- Automate patch deployment: Utilize features that allow for automatic deployment of approved patches.
- Prioritize critical vulnerabilities: Ensure high-risk patches are fast-tracked through the deployment process.
- Monitor and optimize: Continuously track MTTP and identify bottlenecks in your patching process.
Reduction in Security Incidents
Ultimately, the goal of automating 3rd party patching is to enhance security. Measure the impact by tracking:
- Number of security incidents: Monitor for a decrease in incidents related to unpatched vulnerabilities.
- Severity of incidents: Assess whether the automated patching has reduced the occurrence of high-severity security events.
- Incident response time: Evaluate if faster patching has improved your team’s ability to respond to and mitigate threats.
- Audit findings: Track any reduction in patch-related findings during security audits.
Future Trends in Automated 3rd Party Patching
As technology evolves, so too do the approaches to automated 3rd party patching. Stay ahead of the curve by being aware of these emerging trends:
AI and Machine Learning in Patch Management
Artificial Intelligence (AI) and Machine Learning (ML) are set to revolutionize automated patching:
- Predictive analytics: AI algorithms can predict which patches are most likely to cause issues in your specific environment.
- Automated risk assessment: ML models can evaluate the risk of each patch based on historical data and current system states.
- Intelligent scheduling: AI can optimize patch deployment schedules to minimize business disruption.
- Anomaly detection: ML algorithms can quickly identify unusual system behavior post-patching, enabling faster rollbacks if necessary.
Cloud-based Patching Solutions
Cloud technologies are increasingly being leveraged for patch management:
- Scalability: Cloud-based solutions can easily scale to manage large, distributed environments.
- Always up-to-date: Cloud platforms ensure you’re always using the latest version of the patching tool.
- Reduced infrastructure: Cloud solutions minimize the need for on-premises infrastructure dedicated to patch management.
- Global reach: Cloud-based tools can efficiently manage and patch systems across multiple geographic locations.
Integration with Other Security Tools
The future of automated 3rd party patching lies in deeper integration with broader security ecosystems:
- SIEM integration: Patch status and activities will be more tightly integrated with Security Information and Event Management systems.
- Threat intelligence: Patching tools will increasingly consume threat feeds to prioritize patches for actively exploited vulnerabilities.
- Automated incident response: Integration with security orchestration tools will enable automated patching as part of incident response workflows.
- Compliance automation: Deeper integration with compliance tools will streamline auditing and reporting processes.
As these trends continue to shape the landscape of automated 3rd party patching, organizations that stay informed and adapt their strategies accordingly will be best positioned to maintain robust security postures in the face of evolving threats.
Case Studies: Successful Implementation of Automated 3rd Party Patching
To illustrate the real-world impact of automating 3rd party patching, let’s examine two case studies: one from a small business and another from an enterprise-level organization.
Small Business Case Study
Company: TechStart Solutions, a software development startup with 50 employees
Challenge: TechStart was struggling to keep their development environments and employee workstations up-to-date with the latest patches for various programming tools and third-party applications. Their manual patching process was time-consuming and often resulted in missed updates, leading to potential security vulnerabilities.
Solution: TechStart implemented a cloud-based automated patching solution that could handle their diverse software ecosystem. The solution included:
- Automated discovery and inventory of all installed software
- Customizable patching policies for different types of systems (dev environments, workstations)
- Scheduled patch deployments during off-hours
- Detailed reporting for compliance and auditing purposes
Results:
- Reduced time spent on patching by 75%
- Improved patch compliance rate from 60% to 98%
- Decreased mean time to patch critical vulnerabilities from 14 days to 2 days
- No major security incidents related to unpatched vulnerabilities in the 12 months following implementation
Enterprise-level Case Study
Company: GlobalCorp, a multinational corporation with over 50,000 employees across 30 countries
Challenge: GlobalCorp’s IT team was overwhelmed by the task of managing patches for a vast array of third-party applications across their global infrastructure. They faced issues with inconsistent patching, compliance violations, and several security incidents traced back to unpatched vulnerabilities.
Solution: GlobalCorp implemented a comprehensive automated patching solution integrated with their existing IT management tools. Key features included:
- Centralized management console for global patch operations
- Integration with their SIEM and vulnerability management systems
- Automated patch testing in a staging environment before production deployment
- Granular scheduling controls to accommodate different time zones and business hours
- Role-based access control for regional IT teams
Results:
- Achieved 99.5% patch compliance across all systems
- Reduced mean time to patch from 45 days to 5 days for critical vulnerabilities
- Decreased patch-related helpdesk tickets by 60%
- Passed all compliance audits with flying colors in the two years following implementation
- Estimated cost savings of $2 million annually in reduced manual labor and prevented security incidents
Lessons Learned and Best Practices
From these case studies and other successful implementations, we can extract several key lessons and best practices:
- Start with a thorough inventory: A complete and accurate inventory of all systems and software is crucial for effective patching.
- Prioritize and categorize: Develop a clear system for prioritizing patches based on criticality and business impact.
- Test thoroughly: Implement a robust testing process to catch potential issues before they affect production systems.
- Communicate clearly: Keep all stakeholders informed about patching processes, schedules, and potential impacts.
- Monitor and adjust: Continuously monitor your patching metrics and be prepared to adjust your processes as needed.
- Integrate broadly: Look for opportunities to integrate your patching solution with other IT and security tools for maximum efficiency.
- Train your team: Ensure your IT staff is well-trained on the automated patching tools and processes.
Conclusion
Automating 3rd party patching is no longer a luxury—it’s a necessity in today’s complex and rapidly evolving IT landscapes. By implementing a robust automated patching solution, organizations can significantly enhance their security posture, improve operational efficiency, and ensure compliance with industry regulations.
Key takeaways from this comprehensive guide include:
- The critical importance of timely patching for third-party applications
- The numerous benefits of automating the patching process, including improved consistency, efficiency, and security
- Steps to implement an automated patching solution, from assessment to deployment
- Best practices for overcoming common challenges in automated patching
- The importance of measuring and monitoring the success of your patching efforts
- Emerging trends that will shape the future of automated patching
As we’ve seen through case studies and industry trends, organizations of all sizes can benefit from automating their 3rd party patching processes. By embracing automation and following best practices, you can transform patch management from a burdensome task into a streamlined, effective component of your overall security strategy.
Remember, the journey to fully automated 3rd party patching is ongoing. Stay informed about new technologies and trends, continually assess and refine your processes, and prioritize patching as a critical part of your organization’s security posture. With diligence and the right tools, you can significantly reduce your vulnerability to cyber threats and ensure your systems remain secure and up-to-date in an ever-changing digital landscape.