I. Introduction
In today’s rapidly evolving digital landscape, maintaining the security and efficiency of your IT infrastructure is paramount. One of the most critical aspects of this maintenance is patch management. This comprehensive guide will delve into the world of best patch management practices, providing you with the knowledge and tools necessary to safeguard your systems and optimize your IT operations.
Patch management refers to the systematic process of acquiring, testing, and installing updates (patches) for software applications, operating systems, and other IT assets. These patches are designed to fix bugs, address security vulnerabilities, and improve overall system performance. Implementing effective patch management is not just a best practice—it’s a necessity for organizations of all sizes.
Throughout this article, we’ll explore:
- The fundamentals of patch management
- Key components of a robust patch management strategy
- Best tools and solutions for patch management
- Best practices for implementing and maintaining a patch management system
- Strategies for overcoming common challenges
- Future trends in patch management
By the end of this guide, you’ll have a comprehensive understanding of how to implement and maintain the best patch management practices for your organization.
II. Understanding Patch Management
What is a Patch?
At its core, a patch is a piece of software designed to update a computer program or its supporting data. These updates serve various purposes, from fixing security vulnerabilities to improving functionality or performance. Understanding the nature of patches is crucial for implementing effective patch management.
Types of Patches
Patches generally fall into three main categories:
- Security Patches: These address vulnerabilities that could be exploited by malicious actors. They are often the most critical and time-sensitive patches to apply.
- Feature Patches: These introduce new functionality or enhance existing features in software applications or operating systems.
- Bug Fix Patches: These resolve issues or errors in software that may cause crashes, data loss, or other unintended behaviors.
The Importance of Patch Management
Implementing best patch management practices is crucial for several reasons:
- Enhanced Security: Regularly applying security patches helps protect your systems from known vulnerabilities, reducing the risk of data breaches and cyberattacks.
- Improved Performance: Bug fixes and feature updates can enhance system stability and efficiency, leading to better overall performance.
- Compliance: Many regulatory standards require organizations to maintain up-to-date systems. Effective patch management helps ensure compliance with these requirements.
- Cost Reduction: By preventing security incidents and system downtime, good patch management can significantly reduce IT-related costs.
Risks of Poor Patch Management
Neglecting patch management can lead to severe consequences:
| Risk | Potential Impact |
|---|---|
| Security Breaches | Data theft, financial losses, reputational damage |
| System Downtime | Lost productivity, revenue loss, customer dissatisfaction |
| Compliance Violations | Legal penalties, fines, loss of business opportunities |
| Performance Issues | Reduced efficiency, user frustration, increased support costs |
As we delve deeper into best patch management practices, keep in mind that the goal is to create a robust, efficient, and sustainable approach to managing patches across your entire IT infrastructure. This proactive stance will help protect your organization from potential threats and ensure optimal system performance.
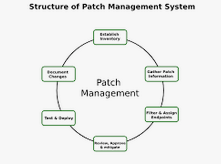
III. Key Components of Effective Patch Management
Implementing the best patch management practices requires a systematic approach. Let’s explore the key components that form the foundation of an effective patch management strategy:
A. Asset Inventory and Management
The first step in any robust patch management process is maintaining an accurate inventory of all IT assets. This includes:
- Hardware devices (servers, workstations, mobile devices)
- Operating systems
- Software applications
- Network devices
An up-to-date asset inventory allows you to identify what needs to be patched, prioritize critical systems, and ensure no device is overlooked. Many organizations use automated asset discovery tools to maintain an accurate and current inventory.
B. Vulnerability Assessment
Regular vulnerability assessments are crucial for identifying potential security weaknesses in your systems. This process involves:
- Scanning systems for known vulnerabilities
- Identifying missing patches
- Assessing the risk level of each vulnerability
- Prioritizing vulnerabilities based on their severity and potential impact
Vulnerability assessment tools can automate much of this process, providing a comprehensive view of your organization’s security posture.
C. Patch Testing
Before deploying patches across your entire network, it’s essential to test them in a controlled environment. This helps identify any potential conflicts or issues that could arise from the patch. The testing process typically includes:
- Setting up a test environment that mirrors your production systems
- Applying patches to test systems
- Conducting thorough testing of all affected applications and processes
- Documenting any issues or conflicts
- Developing mitigation strategies for any identified problems
D. Deployment Strategies
Once patches have been tested and approved, you need a strategy for deploying them across your network. Best patch management practices often include:
- Phased Rollouts: Deploy patches to a small group of non-critical systems first, then gradually expand to larger groups.
- Automated Deployment: Use patch management tools to automate the distribution and installation of patches.
- Scheduled Maintenance Windows: Plan patch deployments during off-hours to minimize disruption to business operations.
- Emergency Patching Procedures: Have a process in place for rapidly deploying critical security patches when necessary.
E. Monitoring and Reporting
The final key component of effective patch management is ongoing monitoring and reporting. This involves:
- Tracking the status of patch deployments
- Monitoring systems for any issues post-patch
- Generating reports on patch compliance and overall security posture
- Regularly reviewing and adjusting your patch management processes based on performance metrics
Implementing these key components will provide a solid foundation for your patch management strategy. However, to truly achieve best patch management practices, you’ll need to complement these components with the right tools and solutions.
IV. Best Patch Management Tools and Solutions
Selecting the right tools is crucial for implementing best patch management practices. Let’s explore some of the top solutions available and what to consider when choosing one:
A. Overview of Top Patch Management Software
Here are some of the leading patch management tools in the market:
- Microsoft System Center Configuration Manager (SCCM): Ideal for Windows-centric environments, offering comprehensive patch management for Microsoft products.
- IBM BigFix: A versatile solution that supports multiple operating systems and applications.
- SolarWinds Patch Manager: Known for its user-friendly interface and integration with Windows Server Update Services (WSUS).
- Ivanti Patch for Windows: Offers automated patch management with detailed reporting capabilities.
- ManageEngine Patch Manager Plus: A cost-effective solution suitable for small to medium-sized businesses.
B. Comparison of Features and Capabilities
When evaluating patch management tools, consider the following key features:
| Feature | Description | Importance |
|---|---|---|
| Multi-platform Support | Ability to manage patches across different operating systems and applications | High |
| Automated Patch Deployment | Capability to schedule and automate patch installations | Critical |
| Reporting and Compliance | Comprehensive reporting features to track patch status and ensure compliance | High |
| Rollback Capability | Ability to revert patches in case of conflicts or issues | Medium |
| Integration with Existing Tools | Compatibility with other IT management and security tools | Medium to High |
C. Factors to Consider When Choosing a Patch Management Tool
When selecting a patch management solution to support your best patch management practices, consider the following factors:
- Scalability: Ensure the tool can grow with your organization and handle your current and future needs.
- Ease of Use: Look for intuitive interfaces and straightforward deployment processes.
- Support and Updates: Choose a vendor that provides reliable support and regular updates to address new vulnerabilities.
- Cost: Consider both the initial investment and long-term costs, including licensing, maintenance, and training.
- Customization: The ability to tailor the tool to your specific needs and workflows can be crucial for some organizations.
- Third-Party Application Support: If you rely heavily on non-Microsoft applications, ensure the tool can manage patches for these as well.
Remember, the best patch management tool for your organization will depend on your specific needs, infrastructure, and resources. Take the time to thoroughly evaluate your options and, if possible, take advantage of free trials before making a decision.
V. Best Practices for Patch Management
Implementing best patch management practices is crucial for maintaining a secure and efficient IT environment. Let’s explore some key strategies that can help you achieve optimal results:
A. Establishing a Patch Management Policy
A comprehensive patch management policy is the foundation of effective patch management. This policy should:
- Define roles and responsibilities within the patch management process
- Establish timelines for patch deployment based on severity
- Outline procedures for testing and approving patches
- Set guidelines for emergency patching scenarios
- Specify documentation and reporting requirements
By clearly defining these aspects, you ensure that everyone involved understands their role in the patch management process.
B. Prioritizing Patches Based on Risk Assessment
Not all patches are created equal. Prioritizing patches based on risk assessment helps focus resources where they’re needed most:
- Critical Security Patches: These should be given the highest priority and deployed as quickly as possible after testing.
- High-Risk Vulnerabilities: Patches addressing significant vulnerabilities should be prioritized next.
- Functional Improvements: Patches that enhance system performance or add new features can be scheduled for regular maintenance windows.
- Low-Risk Updates: Cosmetic changes or minor bug fixes can be deployed during less frequent update cycles.
C. Creating a Patch Testing Environment
A dedicated testing environment is crucial for implementing best patch management practices. This environment should:
- Mirror your production environment as closely as possible
- Include representative samples of all hardware and software configurations
- Allow for thorough testing of patches before deployment
- Provide a space to develop and test rollback procedures
D. Implementing Automated Patch Deployment
Automation is key to efficient patch management. Consider the following steps:
- Use patch management tools to automate the download and distribution of patches
- Set up automatic approval and deployment for low-risk patches
- Configure automated deployment schedules based on patch priority
- Implement automatic reporting to track patch status across your network
E. Scheduling Regular Patch Maintenance Windows
Consistent maintenance windows help minimize disruption and ensure patches are applied regularly:
- Schedule monthly or quarterly maintenance windows for non-critical updates
- Communicate maintenance schedules to all stakeholders well in advance
- Use these windows to apply batches of tested and approved patches
- Consider different time zones and peak usage periods when scheduling
F. Documenting Patch Management Processes
Thorough documentation is essential for maintaining consistency and facilitating audits:
- Document all patch management procedures and policies
- Keep detailed records of all patch deployments, including dates and affected systems
- Maintain logs of any issues encountered and their resolutions
- Regularly review and update documentation to reflect current best practices
VI. Patch Management for Different Environments
Different operating systems and environments require tailored approaches to patch management. Let’s explore best patch management practices for various platforms:
A. Windows Patch Management Best Practices
Microsoft Windows is one of the most common operating systems in enterprise environments. Here are some best practices for Windows patch management:
- Utilize Windows Server Update Services (WSUS) or System Center Configuration Manager (SCCM) for centralized patch management
- Configure automatic updates for workstations, but maintain control over server updates
- Use Group Policy to manage update settings across the network
- Regularly review and clean up superseded updates to maintain system performance
B. Linux Patch Management Strategies
Linux systems require a different approach to patch management:
- Use package managers like YUM (for Red Hat-based systems) or APT (for Debian-based systems) to manage updates
- Implement configuration management tools like Ansible or Puppet for automated patching
- Regularly update repositories and conduct security audits
- Consider using tools like Spacewalk or Canonical Landscape for centralized management of multiple Linux distributions
C. Mac OS Patch Management Techniques
For organizations with Mac devices, consider these patch management techniques:
- Use Apple’s Software Update service or a mobile device management (MDM) solution for centralized control
- Implement Apple’s Device Enrollment Program (DEP) for streamlined deployment and management
- Utilize tools like Jamf Pro or Munki for more advanced management of Mac environments
- Regularly check for and install firmware updates, which are crucial for system security
D. Mobile Device Patch Management Considerations
Mobile devices present unique challenges for patch management:
- Implement a robust Mobile Device Management (MDM) solution
- Enforce policies requiring regular OS updates on company-owned and BYOD devices
- Use containerization or app wrapping to separate and protect corporate data on mobile devices
- Consider using enterprise app stores to control and update in-house mobile applications
E. Cloud Infrastructure Patch Management
Cloud environments require specific considerations for effective patch management:
- Utilize cloud-native tools provided by your cloud service provider (e.g., AWS Systems Manager for Amazon Web Services)
- Implement infrastructure as code (IaC) practices to ensure consistent patching across your cloud infrastructure
- Use immutable infrastructure patterns, replacing entire instances instead of patching in place when possible
- Regularly update both the guest OS and the underlying hypervisor in IaaS environments
By tailoring your patch management approach to each specific environment, you can ensure comprehensive coverage and maintain the security and efficiency of your entire IT infrastructure.
VII. Overcoming Common Patch Management Challenges
Even with best patch management practices in place, organizations often face various challenges. Let’s explore some common issues and strategies to overcome them:
A. Dealing with Legacy Systems
Legacy systems can pose significant challenges for patch management:
- Challenge: Older systems may not support the latest patches or may break when updated.
- Solution:
- Isolate legacy systems on separate network segments
- Implement compensating controls like firewalls and intrusion detection systems
- Consider virtualization to create a more manageable environment for legacy applications
- Develop a long-term plan for system modernization or replacement
B. Managing Patches Across Distributed Networks
Geographically dispersed networks can complicate patch distribution:
- Challenge: Slow WAN links and remote locations can hinder patch distribution.
- Solution:
- Implement local distribution points or caching servers at each major site
- Use peer-to-peer patch distribution technologies to reduce bandwidth usage
- Consider cloud-based patch management solutions for globally distributed networks
- Stagger patch rollouts to manage network load
C. Handling Compatibility Issues
Patches can sometimes cause conflicts with existing software:
- Challenge: Applying a patch may break functionality in other applications.
- Solution:
- Maintain a comprehensive test environment that mirrors production
- Conduct thorough compatibility testing before deploying patches
- Keep detailed documentation of your software inventory and interdependencies
- Develop and test rollback procedures for each patch
D. Balancing Security and Business Continuity
Patch deployment can sometimes disrupt business operations:
- Challenge: Critical systems may not have sufficient downtime for patching.
- Solution:
- Implement redundant systems to allow for rolling updates
- Use live patching technologies where available (e.g., Ksplice for Linux)
- Negotiate planned downtime windows with business stakeholders
- Prioritize patches based on risk assessment to focus on the most critical updates
E. Addressing Resource Constraints
Limited IT resources can hinder effective patch management:
- Challenge: Insufficient staff or expertise to manage the patching process.
- Solution:
- Automate as much of the patch management process as possible
- Consider managed services for patch management
- Prioritize training and skill development for IT staff
- Use risk-based approaches to focus limited resources on the most critical systems
VIII. Patch Management in DevOps and Agile Environments
Modern development practices require a different approach to patch management. Let’s explore how to implement best patch management practices in DevOps and Agile environments:
A. Integrating Patch Management into CI/CD Pipelines
Continuous Integration and Continuous Deployment (CI/CD) pipelines offer opportunities to streamline patch management:
- Incorporate vulnerability scanning into the CI/CD pipeline to identify needed patches early
- Automate the application of patches as part of the build process
- Use infrastructure as code (IaC) to ensure consistent patching across environments
- Implement automated testing to quickly identify any issues introduced by patches
B. Automated Testing for Patches in DevOps
Automation is key to managing patches in fast-paced DevOps environments:
- Develop comprehensive automated test suites that cover critical functionality
- Implement chaos engineering practices to test resilience against unexpected failures
- Use canary deployments to test patches on a small subset of systems before full rollout
- Leverage A/B testing methodologies to compare patched and unpatched systems
C. Balancing Agility and Security in Patch Management
Agile environments require a nimble approach to patch management:
- Adopt a “shift left” mentality, incorporating security and patching considerations earlier in the development process
- Use containerization to create immutable infrastructure, simplifying the patching process
- Implement blue-green deployments to minimize downtime during patching
- Leverage feature flags to quickly disable problematic updates without full rollbacks
“In the world of DevOps, patch management is not a separate process, but an integral part of the entire software lifecycle. It’s about building security and up-to-date systems from the ground up.” – DevOps Institute
By integrating patch management into your DevOps and Agile practices, you can maintain the speed and flexibility these methodologies offer while ensuring your systems remain secure and up-to-date.
IX. Measuring Patch Management Success
To ensure your best patch management practices are effective, it’s crucial to measure and monitor your patch management process. Let’s explore key performance indicators (KPIs), tools, and reporting strategies:
A. Key Performance Indicators (KPIs) for Patch Management
Tracking these KPIs can help you assess the effectiveness of your patch management strategy:
- Patch Coverage Rate: Percentage of systems that have successfully applied all required patches.
- Mean Time to Patch (MTTP): Average time between patch release and successful application across your environment.
- Patch Failure Rate: Percentage of patch installations that fail or cause issues.
- Vulnerability Exposure Time: Duration between a vulnerability’s disclosure and its remediation in your environment.
- Patch Compliance Rate: Percentage of systems meeting defined patching policies and standards.
B. Tools for Tracking Patch Compliance
Several tools can help you monitor and report on patch compliance:
- Vulnerability Scanners: Tools like Nessus or Qualys can identify missing patches across your network.
- Patch Management Platforms: Solutions like Microsoft SCCM or IBM BigFix offer built-in reporting capabilities.
- Security Information and Event Management (SIEM) Systems: These can aggregate patch status data from multiple sources for comprehensive reporting.
- Custom Scripts and Dashboards: For more tailored reporting, you may develop custom tools using PowerShell, Python, or other scripting languages.
C. Reporting and Auditing Patch Management Activities
Regular reporting and auditing are essential for maintaining effective patch management:
- Generate weekly or monthly reports on patch status across your environment.
- Conduct quarterly audits to ensure compliance with patching policies.
- Maintain detailed logs of all patching activities for troubleshooting and compliance purposes.
- Regularly review and update your patch management processes based on these reports and audits.
X. Future Trends in Patch Management
As technology evolves, so do patch management practices. Let’s explore some emerging trends that may shape the future of best patch management:
A. AI and Machine Learning in Patch Management
Artificial Intelligence (AI) and Machine Learning (ML) are poised to revolutionize patch management:
- Predictive analysis to identify systems most likely to experience issues with specific patches.
- Automated risk assessment to prioritize patches based on your specific environment.
- Intelligent scheduling of patches to minimize business disruption.
- Anomaly detection to quickly identify and rollback problematic patches.
B. Predictive Patch Management
Predictive approaches aim to address vulnerabilities before they can be exploited:
- Analyzing patterns in software vulnerabilities to predict future issues.
- Proactive patching based on threat intelligence and vulnerability trends.
- Integration with threat modeling tools to prioritize patches for the most critical assets.
C. Serverless Patch Management
As serverless architectures gain popularity, patch management is evolving:
- Shifting responsibility for underlying infrastructure patching to cloud providers.
- Focus on application-level security and dependencies in serverless environments.
- Automated updating of serverless function runtimes and libraries.
D. Blockchain for Secure Patch Distribution
Blockchain technology may offer new approaches to patch management:
- Secure and tamper-proof distribution of patches.
- Decentralized verification of patch integrity and authenticity.
- Immutable audit trails of patch applications across distributed systems.
XI. Conclusion
Implementing best patch management practices is crucial for maintaining the security, stability, and efficiency of your IT infrastructure. As we’ve explored throughout this guide, effective patch management involves:
- Establishing comprehensive policies and procedures
- Utilizing appropriate tools and automation
- Addressing challenges across diverse environments
- Continuously measuring and improving your patch management processes
- Staying abreast of emerging trends and technologies
By following these best practices and adapting them to your organization’s specific needs, you can significantly reduce your vulnerability to cyber threats, minimize system downtime, and ensure optimal performance of your IT assets.
Remember, patch management is not a one-time task but an ongoing process. As the threat landscape continues to evolve, so too must your patch management strategies. Stay vigilant, stay updated, and prioritize patch management as a critical component of your overall IT and security strategy.
XII. Additional Resources
To further enhance your understanding and implementation of best patch management practices, consider exploring these additional resources:
A. Industry Standards and Guidelines
- NIST Special Publication 800-40: Guide to Enterprise Patch Management Technologies
- CIS Controls v8: Critical Security Controls for Effective Cyber Defense
- ISO/IEC 27001: Information Security Management Systems – Requirements
B. Recommended Books and Whitepapers
- “The Patch Management Book” by Anne E. Kohnke and Daniel G. Stein
- “Mastering Windows Server 2019” by Jordan Krause (includes comprehensive sections on patch management)
- SANS Institute Whitepaper: “Patching as a Public Service: Keeping Systems Up to Date”
C. Relevant Online Courses and Certifications
- CompTIA Security+ (covers patch management as part of broader IT security)
- GIAC Systems and Network Auditor (GSNA)
- Coursera: “IT Security: Defense against the digital dark arts” by Google
By leveraging these resources and continuously educating yourself and your team, you can stay at the forefront of patch management best practices, ensuring your organization’s systems remain secure, stable, and efficient.