I. Introduction
In today’s rapidly evolving digital landscape, organizations face increasingly complex cybersecurity challenges. One of the most critical areas of concern is privileged access management (PAM), which involves controlling and monitoring access to sensitive systems and data. Enter Thycotic Cloud, a cutting-edge solution that’s revolutionizing the way businesses approach PAM in the cloud era.
Thycotic Cloud offers a robust, cloud-based platform for managing privileged access across an organization’s IT infrastructure. As more companies transition their operations to the cloud, traditional on-premises PAM solutions are often found lacking. This is where Thycotic’s cloud-based approach shines, providing a flexible, scalable, and highly secure solution to meet the demands of modern enterprises.
The importance of cloud-based privileged access management cannot be overstated. With cyber threats becoming more sophisticated and the attack surface expanding due to remote work and cloud adoption, organizations need a PAM solution that can keep pace. Thycotic Cloud addresses these challenges head-on, offering a comprehensive suite of tools designed to protect an organization’s most valuable assets.
Key Benefits of Using Thycotic’s Cloud Solution
Adopting Thycotic Cloud for your PAM needs brings numerous advantages:
- Enhanced Security: Leveraging cloud-native security features and continuous updates to protect against the latest threats.
- Scalability: Easily adapt to your organization’s growing needs without the burden of managing additional hardware.
- Cost-Effectiveness: Reduce infrastructure and maintenance costs associated with on-premises solutions.
- Accessibility: Secure access to privileged accounts from anywhere, supporting remote and distributed workforces.
- Compliance: Streamline compliance efforts with built-in reporting and auditing capabilities.
As we delve deeper into the world of Thycotic Cloud, we’ll explore its features, implementation strategies, and best practices for maximizing its potential. Whether you’re a small business looking to enhance your security posture or a large enterprise seeking a more efficient PAM solution, this comprehensive guide will provide valuable insights into how Thycotic Cloud can transform your approach to privileged access management.
II. Understanding Privileged Access Management (PAM)
Before diving deeper into the specifics of Thycotic Cloud, it’s crucial to understand the broader concept of Privileged Access Management (PAM) and its significance in today’s cybersecurity landscape.
Definition of PAM
Privileged Access Management refers to the set of strategies, technologies, and processes used to control, monitor, and secure access to an organization’s critical systems, networks, and data. This access is typically granted to users with elevated privileges, such as system administrators, database managers, or executive-level employees.
PAM solutions like Thycotic Cloud focus on managing these privileged accounts, which often have the highest level of access within an organization’s IT infrastructure. These accounts are prime targets for cybercriminals due to the extensive access and control they provide.
Why PAM is Crucial for Cybersecurity
The importance of robust PAM solutions cannot be overstated in today’s threat landscape. Here’s why PAM is a critical component of any comprehensive cybersecurity strategy:
- Preventing Internal Threats: PAM helps mitigate risks associated with insider threats by controlling and monitoring privileged access.
- Reducing Attack Surface: By limiting and securing privileged access, organizations can significantly reduce their vulnerability to cyber attacks.
- Ensuring Compliance: Many regulatory standards require strict control and auditing of privileged access, which PAM solutions facilitate.
- Improving Visibility: PAM provides detailed insights into privileged account usage, enabling better threat detection and response.
- Streamlining Access Management: Centralized control of privileged accounts enhances efficiency and reduces administrative overhead.
Traditional PAM vs. Cloud-based PAM
As organizations increasingly migrate to cloud environments, the limitations of traditional on-premises PAM solutions become apparent. This is where cloud-based PAM solutions like Thycotic Cloud offer significant advantages:
| Aspect | Traditional PAM | Cloud-based PAM (Thycotic Cloud) |
|---|---|---|
| Deployment | Time-consuming, requires on-site hardware | Rapid deployment, no hardware needed |
| Scalability | Limited by hardware constraints | Highly scalable to meet changing needs |
| Maintenance | Requires regular updates and patches | Automatic updates handled by the provider |
| Accessibility | Often limited to on-premises access | Secure access from anywhere |
| Cost | High upfront costs, ongoing maintenance expenses | Subscription-based, lower total cost of ownership |
Thycotic Cloud represents the next evolution in PAM, offering a solution that’s not only more flexible and cost-effective but also better suited to the distributed nature of modern IT environments. As we continue to explore Thycotic Cloud in more detail, you’ll see how it addresses the challenges of privileged access management in the cloud era, providing a robust and scalable solution for organizations of all sizes.
III. Thycotic Cloud: An Overview
Thycotic Cloud is a comprehensive, cloud-based privileged access management solution designed to meet the evolving security needs of modern organizations. As businesses increasingly migrate their operations to the cloud, traditional on-premises PAM solutions often fall short. This is where Thycotic Cloud steps in, offering a flexible, scalable, and highly secure approach to managing privileged access.
What is Thycotic Cloud?
Thycotic Cloud is a suite of cloud-native privileged access management tools that enable organizations to secure and manage their privileged accounts, passwords, and secrets across diverse IT environments. It provides a centralized platform for controlling access to critical systems, applications, and data, whether they’re hosted on-premises, in the cloud, or in hybrid environments.
Key aspects of Thycotic Cloud include:
- Cloud-Native Architecture: Built from the ground up for cloud environments, ensuring optimal performance and security.
- Comprehensive PAM Capabilities: Offering a full range of privileged access management features in a unified platform.
- Scalability: Easily adaptable to organizations of all sizes, from small businesses to large enterprises.
- Continuous Updates: Regular automatic updates ensure the latest security features and improvements are always available.
- Global Availability: Leveraging cloud infrastructure to provide high availability and performance worldwide.
How Thycotic Cloud Differs from On-Premises Solutions
While Thycotic Cloud shares many core functionalities with its on-premises counterparts, it offers several distinct advantages:
| Feature | Thycotic Cloud | On-Premises Solutions |
|---|---|---|
| Deployment | Rapid, with minimal setup required | Often requires extensive setup and configuration |
| Infrastructure Management | Managed by Thycotic, reducing IT burden | Managed in-house, requiring dedicated resources |
| Scalability | Easily scalable to meet changing needs | Limited by hardware constraints |
| Updates and Maintenance | Automatic, ensuring latest features and security | Manual updates often required |
| Accessibility | Secure access from anywhere with internet connection | Often limited to on-site or VPN access |
| Cost Model | Subscription-based, with predictable pricing | Often involves significant upfront costs |
Key Features of Thycotic Cloud
Thycotic Cloud offers a robust set of features designed to address the complex challenges of privileged access management in modern IT environments:
- Privileged Account Discovery: Automatically identifies and catalogs privileged accounts across your IT infrastructure.
- Password Vault: Securely stores and manages privileged credentials, enforcing strong password policies.
- Session Management: Monitors and records privileged sessions for audit and security purposes.
- Just-in-Time Access: Provides temporary, time-limited access to privileged accounts as needed.
- Multi-Factor Authentication: Adds an extra layer of security for accessing privileged accounts.
- Privileged Behavior Analytics: Detects and alerts on suspicious activities related to privileged access.
- Comprehensive Reporting: Generates detailed reports for compliance and security analysis.
- DevOps Secrets Management: Secures and manages secrets used in DevOps and CI/CD pipelines.
- Cloud Provider Integration: Seamlessly integrates with major cloud platforms like AWS, Azure, and Google Cloud.
By leveraging these features, organizations can significantly enhance their security posture, streamline privileged access workflows, and maintain compliance with various regulatory standards. As we delve deeper into the specifics of Thycotic Cloud in the following sections, you’ll gain a more comprehensive understanding of how these features work together to provide a robust PAM solution for the cloud era.
IV. Core Components of Thycotic Cloud
Thycotic Cloud offers a comprehensive suite of privileged access management tools, each designed to address specific aspects of PAM in cloud environments. Let’s explore the core components that make up this robust solution:
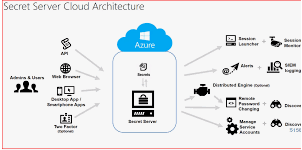
A. Secret Server Cloud
Secret Server Cloud is the cornerstone of Thycotic’s cloud-based PAM offering. This powerful tool provides a centralized vault for storing, managing, and protecting privileged account passwords and other sensitive information.
Key features of Secret Server Cloud include:
- Secure Password Vault: Encrypts and stores passwords using AES 256-bit encryption.
- Role-Based Access Control (RBAC): Granular control over who can access which secrets.
- Password Rotation: Automatically changes passwords on a scheduled basis or after each use.
- Session Recording: Captures and stores privileged sessions for audit and security purposes.
- Discovery: Automatically finds and categorizes privileged accounts across your network.
Secret Server Cloud is particularly valuable for organizations looking to centralize their password management and enhance security around privileged accounts.
B. Privilege Manager Cloud
Privilege Manager Cloud focuses on endpoint privilege management, helping organizations implement least privilege policies and application control.
Notable features of Privilege Manager Cloud include:
- Least Privilege Enforcement: Removes admin rights from endpoints while still allowing users to perform their jobs.
- Application Control: Whitelist or blacklist applications to prevent unauthorized software execution.
- Policy-Based Controls: Create and enforce granular policies for elevated privileges.
- Self-Service Options: Allow users to request elevated privileges when needed, subject to approval workflows.
This component of Thycotic Cloud is crucial for organizations looking to reduce their attack surface by limiting unnecessary privileges on endpoints.
C. DevOps Secrets Vault
As organizations increasingly adopt DevOps practices, the need for secure secrets management in CI/CD pipelines has grown. DevOps Secrets Vault addresses this need within the Thycotic Cloud ecosystem.
Key capabilities include:
- High-Speed Secrets Engine: Designed to meet the performance demands of DevOps environments.
- Dynamic Secrets: Generate temporary, just-in-time credentials for cloud platforms and databases.
- SDK and CLI Support: Easy integration with popular DevOps tools and workflows.
- Cloud Platform Integration: Native support for major cloud providers like AWS, Azure, and GCP.
DevOps Secrets Vault helps organizations maintain security without sacrificing the speed and agility of their DevOps processes.
D. Account Lifecycle Manager
Account Lifecycle Manager automates the process of requesting, approving, and provisioning privileged accounts, streamlining IT operations while maintaining security and compliance.
Key features include:
- Automated Workflows: Streamline the account request and approval process.
- Customizable Approval Chains: Set up multi-level approvals based on your organization’s needs.
- Account Expiration: Automatically disable or remove accounts when they’re no longer needed.
- Integration with Identity Providers: Sync with existing identity management systems for seamless operation.
This component of Thycotic Cloud is particularly valuable for large organizations that need to manage a high volume of privileged accounts across various systems and departments.
“Thycotic Cloud has revolutionized our approach to privileged access management. The integrated suite of tools allows us to maintain tight control over our privileged accounts while providing the flexibility our teams need to work efficiently.”
By combining these core components, Thycotic Cloud provides a comprehensive, cloud-native solution for privileged access management. Each component addresses specific PAM challenges, and when used together, they create a robust security ecosystem that can adapt to the evolving needs of modern IT environments.
V. Benefits of Using Thycotic Cloud
Adopting Thycotic Cloud for your organization’s privileged access management needs brings a multitude of advantages. Let’s explore the key benefits that make this cloud-based PAM solution stand out in the cybersecurity landscape.
A. Scalability and Flexibility
One of the primary advantages of Thycotic Cloud is its inherent scalability and flexibility:
- Elastic Scaling: Easily adapt to changing needs, whether you’re a growing startup or a large enterprise experiencing fluctuations in demand.
- Multi-Cloud Support: Seamlessly manage privileged access across various cloud environments, including AWS, Azure, and Google Cloud.
- Hybrid Compatibility: Integrate with on-premises systems for a unified PAM approach in hybrid IT environments.
This scalability ensures that Thycotic Cloud can grow with your organization, providing consistent security regardless of your infrastructure’s complexity.
B. Reduced Infrastructure Costs
By moving PAM to the cloud, organizations can significantly reduce their infrastructure-related expenses:
- Elimination of Hardware Costs: No need to purchase, maintain, or upgrade on-premises servers dedicated to PAM.
- Reduced IT Overhead: Less time and resources spent on managing and maintaining PAM infrastructure.
- Pay-as-You-Go Model: Only pay for the resources you use, optimizing your PAM spending.
A case study by Thycotic found that organizations using Thycotic Cloud reduced their total cost of ownership for PAM by an average of 40% compared to on-premises solutions.
C. Automatic Updates and Maintenance
Thycotic Cloud takes the burden of updates and maintenance off your IT team:
- Continuous Updates: Always have access to the latest features and security patches without manual intervention.
- Reduced Downtime: Updates are typically performed with minimal or no service interruption.
- Automatic Backups: Regular, automated backups ensure your PAM data is always protected.
This automated approach ensures that your PAM solution is always up-to-date and operating at peak efficiency.
D. Enhanced Security Features
Leveraging cloud technologies, Thycotic Cloud offers advanced security features:
- Multi-Factor Authentication (MFA): Add an extra layer of security for accessing privileged accounts.
- End-to-End Encryption: Protect data in transit and at rest using industry-standard encryption protocols.
- AI-Powered Threat Detection: Utilize machine learning algorithms to identify and alert on suspicious activities.
- Geofencing: Restrict access to privileged accounts based on geographic location.
These features work together to create a robust security posture that can stand up to modern cyber threats.
E. Improved Compliance Management
Thycotic Cloud significantly eases the burden of regulatory compliance:
- Comprehensive Auditing: Detailed logs of all privileged account activities to satisfy audit requirements.
- Pre-built Reports: Generate compliance reports for various standards (e.g., GDPR, HIPAA, PCI DSS) with a few clicks.
- Access Controls: Implement and demonstrate the principle of least privilege across your organization.
- Data Residency Options: Choose where your PAM data is stored to comply with data sovereignty regulations.
A survey conducted by Thycotic revealed that organizations using cloud-based PAM solutions like Thycotic Cloud reported a 35% reduction in time spent on compliance-related tasks.
“Implementing Thycotic Cloud has not only enhanced our security posture but also streamlined our compliance efforts. The automated reporting features have saved our team countless hours during audits.”
By offering these significant benefits, Thycotic Cloud provides a compelling solution for organizations looking to modernize their approach to privileged access management. The combination of enhanced security, reduced costs, and improved operational efficiency makes it a valuable tool in today’s complex cybersecurity landscape.
VI. Implementing Thycotic Cloud in Your Organization
Adopting Thycotic Cloud can significantly enhance your organization’s security posture. However, a successful implementation requires careful planning and execution. This section will guide you through the key steps to effectively implement Thycotic Cloud in your organization.
A. Assessment of Current PAM Needs
Before diving into implementation, it’s crucial to assess your organization’s current privileged access management needs:
- Inventory Privileged Accounts: Identify all privileged accounts across your IT infrastructure, including those in cloud services, on-premises systems, and applications.
- Evaluate Existing Processes: Review your current PAM practices and identify areas for improvement.
- Determine Compliance Requirements: List all relevant compliance standards your organization must adhere to.
- Assess Risk: Conduct a risk assessment to prioritize which systems and accounts need the most urgent protection.
This assessment will provide a clear picture of your PAM requirements and help tailor the Thycotic Cloud implementation to your specific needs.
B. Planning the Migration to Thycotic Cloud
With a clear understanding of your needs, you can now plan the migration to Thycotic Cloud:
- Create a Project Team: Assemble a cross-functional team including IT, security, and relevant business units.
- Define Scope and Objectives: Clearly outline what you want to achieve with the implementation.
- Develop a Phased Approach: Plan a gradual rollout, starting with less critical systems and expanding to more sensitive areas.
- Set a Realistic Timeline: Allow sufficient time for each phase of the implementation, including testing and user training.
A well-planned migration strategy ensures a smooth transition to Thycotic Cloud while minimizing disruption to your operations.
C. Integration with Existing Systems
Thycotic Cloud is designed to integrate seamlessly with a wide range of IT systems and tools. Key integration considerations include:
- Directory Services: Integrate with Active Directory, LDAP, or other identity providers for centralized user management.
- Cloud Platforms: Set up connections with AWS, Azure, Google Cloud, or other cloud services your organization uses.
- SIEM Tools: Integrate with Security Information and Event Management systems for enhanced threat detection and response.
- DevOps Tools: Connect with CI/CD pipelines and container orchestration platforms for secure DevOps practices.
Proper integration ensures that Thycotic Cloud becomes a seamless part of your existing IT ecosystem, maximizing its effectiveness and user adoption.
D. User Training and Adoption Strategies
The success of your Thycotic Cloud implementation largely depends on user adoption. Consider the following strategies:
- Comprehensive Training Program: Develop role-based training sessions to ensure all users understand how to use Thycotic Cloud effectively.
- Create User Guides: Develop easy-to-follow documentation for common tasks and workflows.
- Pilot Program: Start with a small group of users to gather feedback and refine the implementation before full rollout.
- Ongoing Support: Establish a support system to address user questions and issues promptly.
- Measure and Communicate Success: Regularly share metrics on how Thycotic Cloud is improving security to reinforce its importance.
“The key to our successful Thycotic Cloud implementation was our focus on user adoption. By involving end-users early in the process and providing comprehensive training, we achieved over 95% adoption within the first three months.”
Remember, implementing Thycotic Cloud is not just a technical change but also a cultural shift in how your organization approaches privileged access management. By following these steps and focusing on user adoption, you can ensure a successful implementation that enhances your organization’s security posture and streamlines privileged access workflows.
VII. Thycotic Cloud Security Measures
Security is at the core of Thycotic Cloud‘s design. As a solution responsible for managing an organization’s most sensitive access credentials, it employs multiple layers of security to protect your data. Let’s explore the key security measures that make Thycotic Cloud a trusted choice for privileged access management.
A. Data Encryption in Transit and at Rest
Thycotic Cloud employs robust encryption protocols to ensure data security:
- In-Transit Encryption: All data transmitted between your systems and Thycotic Cloud is encrypted using TLS 1.2 or higher, preventing man-in-the-middle attacks and eavesdropping.
- At-Rest Encryption: Data stored within Thycotic Cloud is encrypted using AES 256-bit encryption, one of the strongest encryption standards available.
- Key Management: Encryption keys are securely managed and rotated regularly to maintain the highest level of data protection.
This comprehensive encryption strategy ensures that your sensitive data remains protected at all times, whether it’s being transmitted or stored.
B. Multi-Factor Authentication
To prevent unauthorized access, Thycotic Cloud implements robust multi-factor authentication (MFA) capabilities:
- Multiple MFA Options: Support for various MFA methods, including:
- Time-based One-Time Passwords (TOTP)
- Push notifications to mobile devices
- Hardware tokens
- Biometric authentication
- Contextual Authentication: Ability to require additional authentication factors based on user behavior, location, or device.
- MFA for Critical Operations: Option to require MFA not just for login, but also for sensitive actions within the system.
By implementing strong MFA, Thycotic Cloud significantly reduces the risk of unauthorized access, even if passwords are compromised.
C. Role-Based Access Control
Thycotic Cloud employs a granular role-based access control (RBAC) system to ensure users only have access to the resources they need:
- Customizable Roles: Create roles tailored to your organization’s specific needs and structure.
- Least Privilege Principle: Easily implement and maintain a least privilege model across your organization.
- Separation of Duties: Enforce segregation of duties to prevent any single user from having excessive control.
- Dynamic Access Control: Adjust user permissions in real-time based on changes in roles or responsibilities.
This RBAC system allows for precise control over who can access what within your Thycotic Cloud environment, minimizing the risk of insider threats and accidental misuse.
D. Audit Logs and Reporting
Comprehensive auditing and reporting capabilities are crucial for maintaining security and compliance. Thycotic Cloud offers:
- Detailed Activity Logs: Every action within the system is logged with relevant details such as user, time, and IP address.
- Tamper-Evident Logging: Logs are cryptographically signed to prevent unauthorized modifications.
- Real-Time Alerts: Set up alerts for suspicious activities or policy violations.
- Customizable Reports: Generate reports tailored to your specific compliance and auditing needs.
- Log Retention: Maintain logs for extended periods to meet regulatory requirements and support forensic investigations.
These auditing and reporting features not only enhance security but also streamline compliance efforts and support incident response processes.
“The comprehensive security measures in Thycotic Cloud, especially its robust encryption and granular access controls, were key factors in our decision to adopt the platform. It’s given us confidence in the security of our privileged access management.”
By implementing these multi-layered security measures, Thycotic Cloud provides a secure environment for managing privileged access. The combination of strong encryption, multi-factor authentication, role-based access control, and comprehensive auditing creates a robust security posture that can withstand sophisticated cyber threats while meeting stringent compliance requirements.
As cyber threats continue to evolve, Thycotic Cloud regularly updates its security measures to stay ahead of potential vulnerabilities, ensuring that your organization’s most sensitive access credentials remain protected at all times.